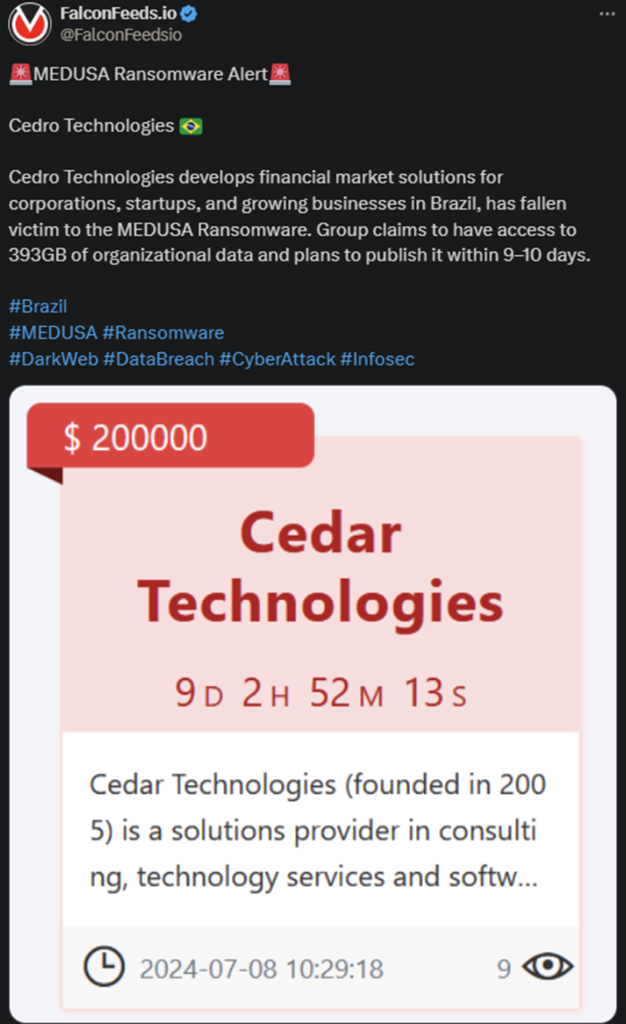
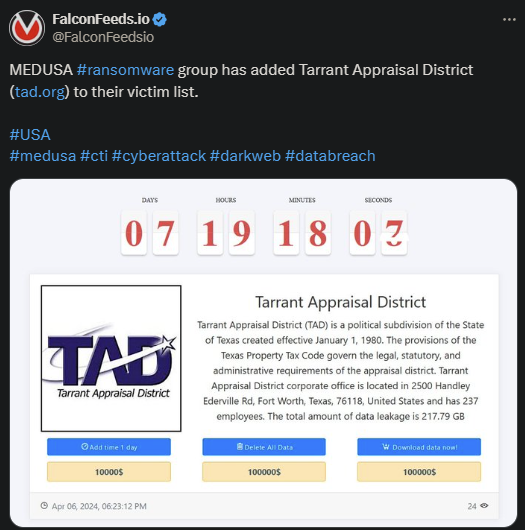
Cybersecurity professionals are issuing urgent alerts regarding a significant and highly perilous threat: Medusa ransomware. This advanced malware has the potential to severely disrupt and compromise the operations of both organizations and individuals, demanding exorbitant ransoms in exchange for decrypting essential data. As the frequency and complexity of cyberattacks continue to escalate, gaining a comprehensive understanding of Medusa ransomware is crucial for safeguarding your digital assets and ensuring robust online security.
Medusa ransomware has surfaced as one of the most alarming cybersecurity threats in recent years. By encrypting critical files and demanding substantial payments for decryption keys, this malicious software poses a formidable challenge to businesses and individuals alike. This article delves into the intricacies of Medusa ransomware, exploring its mechanisms, implications, and providing practical steps to protect yourself from falling victim to this harmful software.
In today's rapidly evolving digital landscape, staying informed about emerging threats is essential for effective defense. This guide offers an in-depth examination of Medusa ransomware, tracing its origins and the potential damage it can inflict. Whether you're a business owner, an IT professional, or an individual seeking to enhance your online security, this resource will equip you with the knowledge and tools necessary to secure your digital environment.
Read also:Palmeiras Vs Corinthians A Celebration Of Brazilian Footballs Iconic Rivalry
Table of Contents
- Introduction to Medusa Ransomware
- History and Origins of Medusa Ransomware
- Impact of Medusa Ransomware Attacks
- How Medusa Ransomware Works
- Prevention Strategies Against Medusa Ransomware
- Recovery Options After an Attack
- Business Risks Associated with Medusa Ransomware
- Government and Official Responses
- Best Practices for Cybersecurity
- Future Trends in Ransomware
Unveiling Medusa Ransomware: A Modern-Day Cyber Threat
Medusa ransomware represents a new frontier in cybercrime, designed to exploit vulnerabilities within digital infrastructures. Once it infiltrates a system, it encrypts files, rendering them inaccessible until a ransom is paid. The attackers behind Medusa ransomware typically demand payment in cryptocurrencies, complicating efforts to trace their activities and hold them accountable.
This particular strain of ransomware is especially dangerous due to its dual targeting of individuals and businesses, with the ability to cause significant financial and operational harm. Unlike earlier versions of ransomware, Medusa employs cutting-edge encryption techniques and spreads rapidly across networks, making containment a significant challenge.
Why Medusa Ransomware is a Growing Concern
Cybersecurity authorities are sounding the alarm as Medusa ransomware attacks are increasing in frequency and sophistication. Recent statistics indicate a staggering 30% rise in incidents involving Medusa ransomware over the past year. This troubling trend underscores the urgent need for heightened awareness and proactive cybersecurity measures.
- Medusa ransomware targets critical data, including sensitive financial records and personal information.
- It spreads swiftly through networks, affecting multiple devices simultaneously.
- Attackers demand exorbitant ransoms, frequently exceeding tens of thousands of dollars.
The Emergence and Evolution of Medusa Ransomware
The origins of Medusa ransomware can be traced to a sophisticated group of cybercriminals based in Eastern Europe. Known for their innovative strategies in cybercrime, these attackers have continuously refined their tactics to bypass even the most advanced security protocols. Medusa ransomware made its debut in early 2022, quickly earning notoriety for its effectiveness and the substantial ransoms it demands.
Key Milestones in the Development of Medusa Ransomware
- 2022: Initial detection of Medusa ransomware in a series of high-profile attacks.
- 2023: A surge in attacks targeting small and medium-sized businesses.
- 2024: Expansion into critical infrastructure sectors, notably healthcare and finance.
An in-depth understanding of Medusa ransomware's history is crucial for predicting future trends and devising effective countermeasures. Cybersecurity experts are closely monitoring its evolution to uncover potential vulnerabilities and develop comprehensive strategies to mitigate its impact.
Read also:Exploring The Thrilling World Of Sec Basketball
The Catastrophic Impact of Medusa Ransomware Attacks
Medusa ransomware attacks can have devastating consequences for both individuals and organizations. Beyond the immediate financial burden of paying ransoms, victims often face long-term repercussions, such as reputational damage and operational disruptions.
Economic Consequences
Businesses that fall victim to Medusa ransomware attacks often experience significant financial losses. These losses extend beyond ransom payments to include costs associated with downtime, data recovery, and potential legal liabilities. A report by Cybersecurity Ventures forecasts that the global cost of ransomware attacks could exceed $20 billion by 2024.
Operational Disruptions
Medusa ransomware has the capacity to incapacitate an organization's operations by encrypting critical files and systems. This often results in prolonged periods of downtime, affecting productivity and customer service delivery. For businesses in sectors like healthcare and finance, the consequences can be even more severe, as they may be unable to provide essential services.
Understanding the Mechanics of Medusa Ransomware
Medusa ransomware operates by exploiting vulnerabilities in software and network systems. Once it infiltrates a system, it begins encrypting files and displays a ransom note demanding payment for the decryption key. The attackers utilize a variety of techniques to breach systems, such as phishing emails, malicious downloads, and exploiting unpatched software vulnerabilities.
Common Entry Points for Medusa Ransomware
- Phishing emails containing malicious attachments or links.
- Unpatched software vulnerabilities.
- Weak passwords and inadequate access controls.
A thorough understanding of how Medusa ransomware operates is vital for developing effective prevention strategies. By identifying and addressing potential entry points, organizations can significantly reduce their risk of infection and minimize the impact of potential attacks.
Effective Strategies for Preventing Medusa Ransomware Attacks
Preventing Medusa ransomware attacks requires a multi-faceted approach, combining both technical and organizational measures. Cybersecurity experts recommend implementing a blend of proactive measures to mitigate the risk of infection and lessen the impact of potential breaches.
Technical Measures
- Regularly update and patch software to address known vulnerabilities.
- Deploy robust antivirus and anti-malware solutions.
- Implement network segmentation to restrict the spread of infections.
Organizational Measures
- Conduct regular cybersecurity training sessions for employees.
- Establish and enforce stringent password policies.
- Develop and implement an incident response plan to address potential attacks.
By integrating technical and organizational measures, organizations can build a comprehensive defense against Medusa ransomware and other cyber threats.
Recovering After a Medusa Ransomware Attack
In the event of a Medusa ransomware attack, prompt action is critical to minimize damage and recover lost data. Cybersecurity experts recommend following a structured recovery process, including assessing the scope of the attack, restoring data from backups, and implementing additional security measures to prevent future incidents.
Steps for Effective Recovery
- Isolate infected systems to prevent further propagation.
- Restore data from secure backups, if available.
- Engage cybersecurity experts to analyze the attack and suggest improvements.
Recovering from a Medusa ransomware attack can be a complex and challenging process. However, with the right tools and expertise, organizations can regain control of their systems and fortify their defenses against future threats.
The Risks Businesses Face from Medusa Ransomware
Businesses encounter numerous risks when dealing with Medusa ransomware, ranging from financial losses to reputational harm. These risks can have lasting effects, impacting customer trust and market competitiveness. Cybersecurity experts emphasize the importance of risk management strategies to mitigate these potential consequences.
Financial Risks
Financial losses from Medusa ransomware attacks can be substantial, encompassing the costs of ransom payments, data recovery, and legal liabilities. Organizations must carefully assess these risks and implement insurance and financial safeguards to protect against potential losses.
Reputational Risks
Reputational damage can be one of the most significant outcomes of a Medusa ransomware attack. Customers and partners may lose confidence in an organization's ability to safeguard sensitive data, leading to a decline in business opportunities and customer loyalty. Addressing these risks involves proactive communication and transparency in the aftermath of an attack.
Government Initiatives and Official Responses to Medusa Ransomware
Governments and cybersecurity authorities worldwide are taking decisive steps to combat the escalating threat of Medusa ransomware. These efforts include enhanced collaboration between law enforcement agencies, the development of new cybersecurity regulations, and the promotion of public awareness campaigns.
International Cooperation
International collaboration is crucial in the fight against Medusa ransomware. Cybercriminals often operate across borders, necessitating cooperation between governments to track and apprehend attackers. Initiatives like the International Cybersecurity Alliance aim to strengthen cooperation and facilitate information sharing between nations.
New Regulations and Guidelines
Governments are also introducing new regulations and guidelines to assist organizations in protecting themselves against Medusa ransomware. These measures include mandatory reporting requirements for cyber incidents and standards for cybersecurity best practices. By adhering to these regulations, organizations can enhance their defenses and safeguard both themselves and their customers from cyber threats.
Best Practices for Enhancing Cybersecurity
Adopting best practices for cybersecurity is essential for protecting against Medusa ransomware and other cyber threats. Cybersecurity experts recommend a combination of technical, organizational, and educational measures to establish a robust defense against cyberattacks.
Technical Best Practices
- Implement multi-factor authentication for all systems and applications.
- Regularly back up critical data and store backups in secure, offsite locations.
- Monitor network activity for signs of suspicious behavior.
Organizational Best Practices
- Promote a culture of cybersecurity awareness within your organization.
- Develop and enforce policies for safe internet usage and data handling.
- Engage with cybersecurity experts to stay informed about emerging threats.
By following these best practices, organizations can significantly reduce their risk of falling victim to Medusa ransomware and other cyber threats.
Predicting the Future of Ransomware: Trends and Threats
The trajectory of ransomware, including Medusa ransomware, is expected to involve even more advanced attacks and increased targeting of critical infrastructure. Cybersecurity experts predict that attackers will continue to adapt their tactics, leveraging artificial intelligence and machine learning to bypass traditional security measures.
Emerging Threats
Emerging threats in the realm of ransomware include AI-powered attacks, targeting cloud-based systems, and exploiting vulnerabilities in IoT devices. Organizations must remain vigilant and proactive in addressing these potential vulnerabilities to protect their digital assets.
Adapting to Future Threats
To adapt to future trends in ransomware, organizations should invest in state-of-the-art cybersecurity technologies and stay abreast of the latest developments in the field. By fostering a culture of continuous learning and improvement, organizations can better prepare themselves for the ever-evolving landscape of cyber threats.
Conclusion
Medusa ransomware poses a significant threat to individuals and organizations worldwide. By understanding its origins, impact, and mechanisms, we can develop effective strategies to prevent and recover from attacks. Cybersecurity experts emphasize the importance of proactive measures, such as regular software updates, employee training, and incident response planning, to mitigate the risks associated with Medusa ransomware.
We encourage readers to take action by implementing the best practices outlined in this article and staying informed about the latest developments in cybersecurity. By working collaboratively, we can create a safer digital environment for everyone. Please share this article with your colleagues and friends, and consider exploring our additional resources on cybersecurity for further guidance.