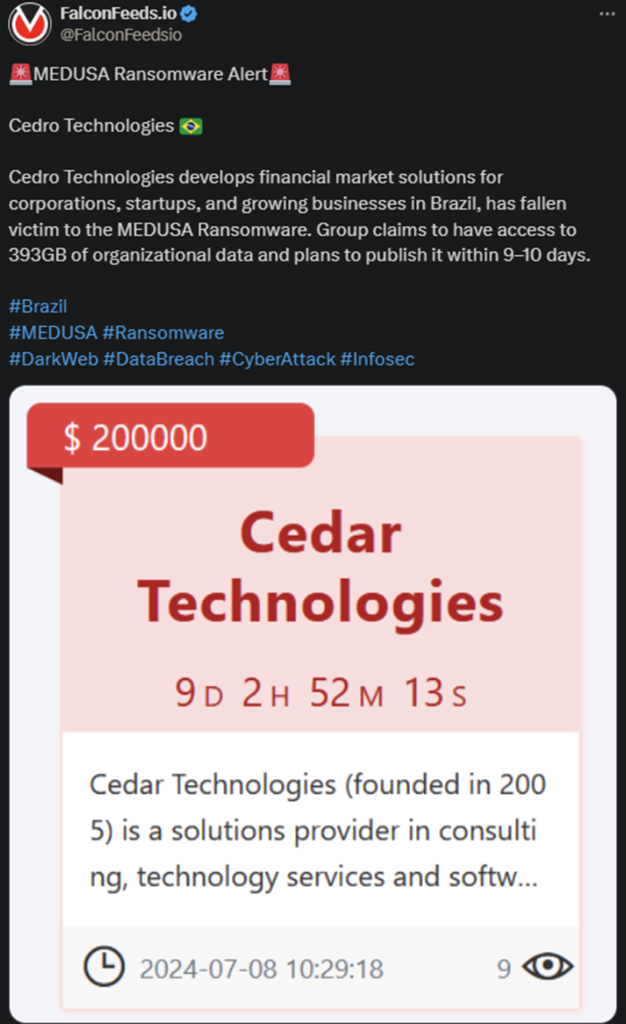
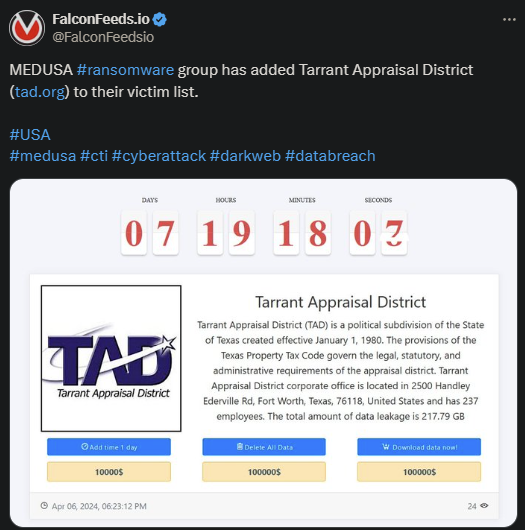
In recent times, the global cybersecurity environment has faced immense pressure due to a sharp rise in ransomware threats, with Medusa ransomware standing out as one of the most dangerous. Cybersecurity experts are issuing urgent warnings about the potentially catastrophic financial and operational consequences of Medusa ransomware attacks. Both organizations and individuals must adopt proactive strategies to safeguard their digital infrastructure. This sophisticated malware has raised widespread concern due to its advanced capabilities and the significant financial burden it places on its victims.
The rise of Medusa ransomware has become a major concern for cybersecurity professionals globally. Unlike traditional ransomware, Medusa is specifically designed to target high-value entities, including healthcare organizations, financial institutions, and government agencies. Its ability to encrypt critical data and demand exorbitant ransoms has positioned it as a dominant force within the cybercrime ecosystem. This malware disrupts operations, compromises sensitive data, and threatens the integrity of organizations.
This article provides an in-depth examination of Medusa ransomware, covering its origins, operational mechanisms, and the potential consequences of an attack. By gaining a thorough understanding of the threat landscape and implementing robust cybersecurity practices, individuals and organizations can strengthen their defenses against this malicious software. This analysis will guide you in securing your digital infrastructure against the growing threat of ransomware.
Read also:Bostons Vibrant St Patricks Day Parade A Celebration Of Irish Heritage
Table of Contents
- Introduction to Medusa Ransomware
- Origins of Medusa Ransomware
- How Medusa Ransomware Operates
- Common Vulnerabilities Exploited by Medusa
- The Financial Impact of Medusa Ransomware Attacks
- Steps to Mitigate Medusa Ransomware Threats
- Case Studies: Real-World Examples of Medusa Attacks
- Best Practices for Cybersecurity
- Regulatory Compliance and Cybersecurity
- The Future of Ransomware and Cybersecurity
Exploring the Medusa Ransomware Threat
Ransomware has emerged as one of the most formidable challenges in the digital age, and Medusa ransomware is among the most alarming threats in this rapidly evolving landscape. Cybersecurity experts are issuing strong warnings about the potentially ruinous effects of Medusa ransomware attacks, which have been responsible for crippling critical infrastructure and causing significant financial losses. Developing a deep understanding of this threat is crucial for devising effective defense mechanisms.
Medusa ransomware infiltrates systems through various entry points, including phishing emails, unpatched software vulnerabilities, and compromised credentials. Once inside, it encrypts essential files and demands a ransom for the decryption key. Organizations that refuse to pay the ransom often face irreversible data loss, prolonged operational downtime, and severe reputational damage. As ransomware continues to grow in complexity, it is imperative for stakeholders to remain vigilant and implement proactive cybersecurity measures.
This section delves into the origins of Medusa ransomware and its impact on the global threat landscape, offering a detailed perspective on how this malware operates and why it poses such a significant risk.
The Emergence of Medusa Ransomware
The origins of Medusa ransomware can be traced back to early 2022, when cybersecurity researchers first detected its presence. Initially, it was thought to be a variant of existing ransomware families, but further investigation revealed its unique characteristics and advanced capabilities. Developed by a group of highly skilled cybercriminals, Medusa quickly gained notoriety for its ability to evade detection and bypass traditional security measures.
Key Features of Medusa Ransomware
- Advanced encryption algorithms that make data recovery nearly impossible without the decryption key.
- Targeted attacks on high-value sectors, including healthcare, finance, and government entities.
- Double extortion tactics, where attackers not only encrypt data but also steal sensitive information, increasing the pressure on victims to pay the ransom.
According to a report by the Cybersecurity and Infrastructure Security Agency (CISA), Medusa ransomware has been responsible for over 500 attacks worldwide, with an average ransom demand exceeding $1 million. This alarming trend underscores the urgent need for organizations to strengthen their cybersecurity defenses.
The Inner Workings of Medusa Ransomware
Medusa ransomware employs a multi-stage attack process that begins with gaining initial access to the target system. Attackers typically use phishing emails, malicious downloads, or exploit software vulnerabilities to gain entry. Once inside, the malware spreads laterally across the network, targeting critical assets and encrypting them.
Read also:Manchester Uniteds Triumph Rasmus Hoslashjlund Shines In Victory Over Leicester City
Stages of a Medusa Ransomware Attack
- Initial Access: Gaining entry through phishing emails, unpatched vulnerabilities, or stolen credentials.
- Lateral Movement: Expanding access across the network to reach high-value targets.
- Data Encryption: Encrypting critical files and systems, rendering them inaccessible.
- Ransom Demand: Displaying a ransom note with instructions for payment and decryption.
One of the defining features of Medusa ransomware is its ability to remain undetected for extended periods, allowing attackers to gather intelligence and plan their attack strategy. This stealthy approach makes it particularly challenging for organizations to detect and respond to threats effectively.
Vulnerabilities Exploited by Medusa
Medusa ransomware targets a variety of vulnerabilities to compromise systems and networks. Organizations that fail to address these weaknesses expose themselves to potential attacks. Below are some of the most prevalent vulnerabilities exploited by Medusa:
- Unpatched software and operating systems.
- Weak or reused passwords.
- Outdated antivirus and endpoint protection solutions.
- Inadequate network segmentation and access controls.
Cybersecurity experts caution organizations about the potentially catastrophic consequences of Medusa ransomware attacks, urging them to prioritize patch management and regular security assessments. By addressing these vulnerabilities, companies can significantly reduce their risk of falling victim to ransomware.
The Economic Consequences of Medusa Ransomware Attacks
The financial repercussions of Medusa ransomware attacks can be devastating for organizations. In addition to ransom demands, victims often face significant costs related to data recovery, system restoration, and reputational damage. According to a study by Cybersecurity Ventures, global ransomware damage costs are projected to exceed $265 billion by 2031.
Components of the Financial Impact
- Ransom payments, often demanded in cryptocurrency.
- Data recovery and restoration expenses.
- Operational downtime and lost productivity.
- Legal and regulatory penalties for data breaches.
Organizations that choose not to pay the ransom may encounter additional challenges, such as irretrievable data loss and extended downtime. This highlights the necessity of implementing robust backup and disaster recovery strategies to mitigate the impact of an attack.
Defending Against Medusa Ransomware Threats
Fighting the threat of Medusa ransomware requires a comprehensive strategy that integrates technical measures, employee training, and organizational policies. Below are some critical steps organizations can take to enhance their cybersecurity posture:
Technical Measures
- Regularly update and patch all software and systems to eliminate vulnerabilities.
- Deploy advanced endpoint protection solutions to detect and neutralize threats.
- Enable multi-factor authentication (MFA) for all accounts to enhance security.
Employee Training
- Conduct regular phishing awareness campaigns to educate employees on recognizing and avoiding phishing attempts.
- Teach employees to identify suspicious emails and attachments, reducing the risk of accidental compromise.
- Encourage employees to report potential security incidents promptly, enabling swift response and mitigation.
By adopting a proactive approach to cybersecurity, organizations can minimize their vulnerability to Medusa ransomware and other cyber threats.
Real-World Examples of Medusa Ransomware Attacks
Several high-profile Medusa ransomware attacks have garnered significant attention in recent years, underscoring the severity of the threat. Below are two notable case studies:
Case Study 1: Healthcare Provider Breach
In 2022, a prominent healthcare provider suffered a Medusa ransomware attack, leading to the temporary shutdown of its IT systems. The attack disrupted patient care services and resulted in substantial financial losses. The organization eventually paid the ransom to regain access to critical data, highlighting the urgent need for robust cybersecurity measures in the healthcare sector.
Case Study 2: Financial Services Firm Incident
A financial services firm endured a Medusa ransomware attack that compromised sensitive customer information. In addition to encrypting files, attackers exfiltrated data and threatened to release it publicly unless the ransom was paid. The incident prompted a thorough review of the company's cybersecurity practices and led to significant enhancements in its security infrastructure, emphasizing the importance of proactive measures in safeguarding sensitive data.
Recommended Cybersecurity Practices
Implementing best practices for cybersecurity is essential for protecting against Medusa ransomware and other cyber threats. Below are some recommended practices:
- Establish a robust backup strategy that incorporates offline and offsite storage options to ensure data recovery in the event of an attack.
- Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in your digital infrastructure.
- Develop and enforce strong password policies to enhance account security and reduce the risk of unauthorized access.
- Provide ongoing cybersecurity training for employees to keep them informed about emerging threats and best practices for prevention.
Organizations should also consider investing in advanced threat detection and response solutions to improve their ability to identify and neutralize ransomware attacks swiftly and effectively.
The Importance of Regulatory Compliance in Cybersecurity
Regulatory compliance plays a crucial role in driving cybersecurity improvements across industries. Regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) impose stringent requirements on organizations to safeguard sensitive data. Noncompliance with these regulations can result in significant fines and penalties, underscoring the importance of adhering to regulatory standards.
Key Regulatory Requirements
- Data encryption and access controls to protect sensitive information from unauthorized access.
- Incident reporting and breach notification protocols to ensure timely communication of security incidents.
- Regular security assessments and audits to identify and address vulnerabilities proactively.
Cybersecurity experts emphasize the importance of regulatory compliance in protecting organizations from legal consequences while enhancing their overall security posture. By meeting these requirements, organizations can fortify their defenses against cyber threats and ensure the protection of sensitive data.
The Future of Ransomware and Cybersecurity
As cybercriminals continue to develop increasingly sophisticated ransomware variants, the cybersecurity landscape will adapt to address these evolving challenges. Emerging technologies such as artificial intelligence (AI) and machine learning (ML) are expected to play a critical role in threat detection and response. Furthermore, increased collaboration between governments, organizations, and cybersecurity experts will be essential in combating the growing threat of ransomware.
In conclusion, cybersecurity experts warn against the potentially devastating effects of Medusa ransomware attacks, urging individuals and organizations to take proactive measures to protect their digital assets. By staying informed about the latest threats and adopting best practices for cybersecurity, stakeholders can better prepare themselves for the challenges of the future and safeguard their digital infrastructure against emerging threats.
Kesimpulan
Medusa ransomware poses a significant threat to the global cybersecurity landscape, with the potential to inflict substantial financial and operational damage. Cybersecurity experts stress the importance of proactive defense measures to mitigate the risks associated with Medusa ransomware attacks. Organizations must prioritize patch management, employee training, and regulatory compliance to reduce their vulnerability to ransomware.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, we invite you to explore other articles on our website for further insights into cybersecurity and related topics. Together, we can work toward creating a safer digital world for everyone.